The report “Police-reported crime statistics in Canada, 2016” by Kathryn Keighley at the Canadian Centre for Justice Statistics is available from the station website. This report was released the 24th of July 2017. With regards to cybercrime the report includes the following In 2016, the number and rate of child pornography incidents continued …
There is a considerable amount of evidence on the control and censorship of social media in China. On top of this there has long been suspected that there is a system of astroturfing, or the posting of large numbers of comments from fake accounts to direct online conversation. In China people hired to make these …
Jonathon Lusthaus and Federico Varese provide more insight into the phenomena of online crime groups. To provide more of an understanding of the offline nature of online groups they took two field trips to Romania to investigate the region around Râmnicu Vâlcea, a local known for cybercrime. The Region of Ca Piteşti, which contains this …
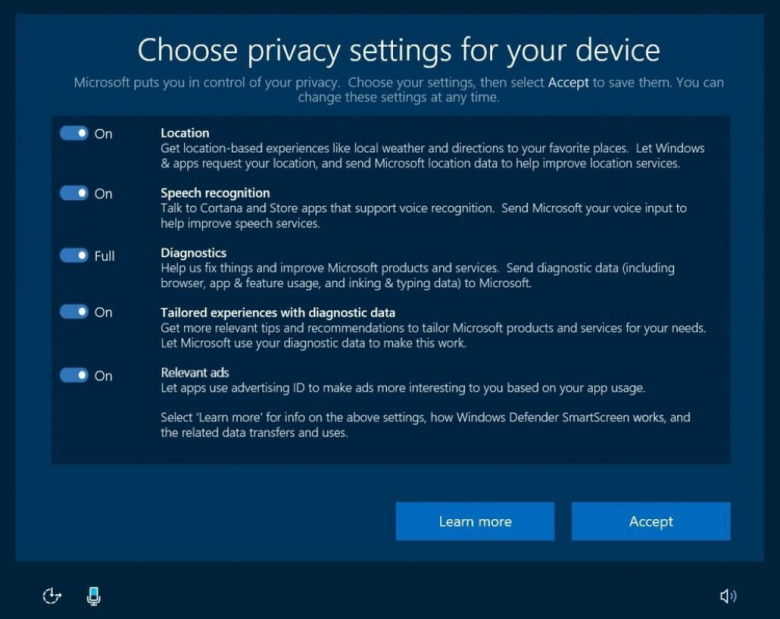
First, today we’re launching a new web-based privacy dashboard so you can see and control your activity data from Microsoft including location, search, browsing, and Cortana Notebook data across multiple Microsoft services. Second, we’re introducing in Windows 10 a new privacy set up experience, simplifying Diagnostic data levels and further reducing the data collected at …
“What I can say is there are many ways to surveil each other,” Ms. Conway told the paper. “You can surveil someone through their phones, certainly through their television sets — any number of ways.” Surveillance can even be carried out with “microwaves that turn into cameras,” she added. “We know this is a fact …
13th annual GoSec Cyber Security Conference. GoSec brings together experts in the information technology security field from multiple sectors. This year SERENE-RISC will be presenting a tutorial ( Examining Cybercrime 3: SME Edition) to complement this well established and well attended annual event. Details at : https://www.serene-risc.ca/en/events/professional-development/examining-cybercrime-3-sme-edition Event Time: AUGUST 30TH AND 31ST, 2017 8:00 am until …
Short answer is bad, but for more reasons than first come to mind. Wikileaks recently released a vault of documents allegedly from the CIA relating to their cyber capabilities[1]. This is not the first time that Wikileaks has released fairly targeted documents against an agency in the United States[2][3][4][5]. Wikileaks founder Julian Assange has clear …
A group from Northwest University, China, and the University of Bath and Lancaster University in the UK have come up with a method for determining android unlock patterns. The method uses video footage captured by a smartphone and an algorithm that can determine likely codes that match the movement of the finger or hand across …
Vinay Kaura provides some insight into the impact of the Internet on insurgency in the region of Kashmir. This region has famously been in conflict for more than half a century and has crossed over into the digital realm. The problems are deeply complex and the informatization of the region has created additional layers with …
A keynote address by Erinn Clark, Lead Security Architect, First Look Media/The Intercept More than 80 refereed paper presentations as well as invited talks, a poster session, a doctoral colloquium, a Work-in-Progress session, and Birds-of-a-Feather sessions. Sheraton Vancouver Wall Centre Hotel 1088 Burrard Street Vancouver, BC, V6Z 2R9 Canada https://www.usenix.org/conference/usenixsecurity17