The Internet of Things (IoT), cloud computing technology, and health technologies are essential tools in 2021 to ensure the well-being and running of individuals and organizations’ activities in our society. However, considering the importance of connected objects and the irreplaceable place they occupy, it is vital to ensure that they are well protected against malware …
L’internet des objets (IoT) (« Internet of things » en anglais), la technologie par nuagerie informatique et les technologies de santé sont des outils primordiaux en 2021 pour assurer le bien-être et le roulement des activités des individus et des organisations primordiales dans notre société. Considérant l’importance des objets connectés, et la place irremplaçable qu’ils occupent, il …
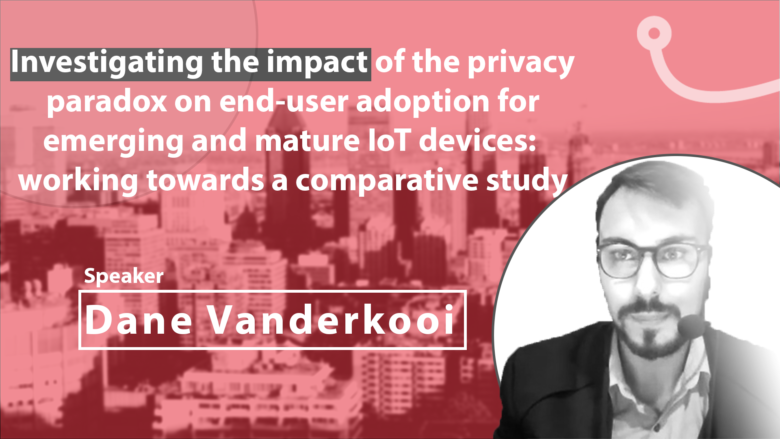
Presented by Dane Vanderkoi as a part of the 2020 Serene-risc Workshop on The State of Canadian Cybersecurity Conference: Human-Centric Cybersecurity About the presentation Recent years have seen the rise of a new group of technologies known as IoT (Internet of Things). IoT devices seamlessly connect and share information, providing additional functionality and convenience for …
Presented by Chris Bellman as a part of the 2020 Serene-risc Workshop on The State of Canadian Cybersecurity Conference: Human-Centric Cybersecurity About the presentation Recently, best practices for Internet of Things (IoT) security have shown to be of interest to government and industry organizations. Academic research has highlighted a failure to follow established security practices, …
De nombreux appareils variés s’appuyant sur l’Internet des objets continuent de proliférer sur le marché. Les appareils domestiques intelligents aux multiples avantages sont commercialisés pour faciliter la vie des consommateurs et représentent par conséquent une part importante du marché de l’Internet des objet grand public. Les médias et les chercheurs ont soulevé des questions quant …
Numerous and various interconnected Internet of Things (IoT) devices continue to increase on the market. Smart home devices are marketed as providing multiple benefits to make consumers’ life more manageable and, as such, are a significant part of the loT consumer market. Media and researchers have raised questions about the security of smart home technology, …
Understanding the Simplicity Behind IoT Botnets: A Case Study of a Social Media Fraud Provider Masarah Paquet-Clouston, GoSecure Presented at the SERENE-RISC Workshop, April 2017 Who would want to be liked by an army of robots? The size of a social media account’s audience is considered to be a measure of the influence of a …
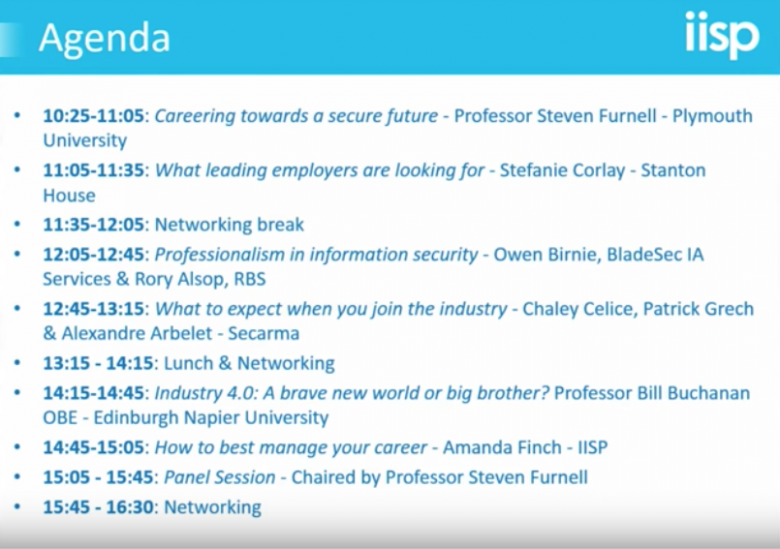
The IISP (Institute of Information Security Professionals) and our friends the Cyberacademy at Napier College, Edinburgh, Scotland recently (2017/11/23) held an event for those looking to start or continue a career in cybersecurity. The event had a number of great presenters and fortunately for us was streamed to youtube. The full video is over 5 …
Short answer is bad, but for more reasons than first come to mind. Wikileaks recently released a vault of documents allegedly from the CIA relating to their cyber capabilities[1]. This is not the first time that Wikileaks has released fairly targeted documents against an agency in the United States[2][3][4][5]. Wikileaks founder Julian Assange has clear …