Cormac Herley presents work done with Paul van Oorshot on some historic ideas that might help us work towards a common science for information security. This is something that we all need in order to progress the field. “Claims that uniques aspects of security exempt it from a scientific approach are unhelpful.” There has been …
Month: December 2017
A recent podcast from risky business (www.risky.biz) had a very interesting interview with Stephen Morse, formerly the staff vice president of cybersecurity analytics at Anthem. You might remember that Anthem were the target of a state-sponsored attack back in 2015. The interview is well worth listening, particularly for those charged with security in a large …
How are those with intellectual disabilities affected by cyberbullying? The research team of Cristina Jenaro, Noelia Flores, Vanessa Vegab Maribel Cruz, Ma. Carmen Pérez, and Víctor A. Torres from the Universidad de Salamanca in Spain, the Pontificia Universidad Católica de Valparaíso in Chile, and the Universidad Autónoma de San Luis Potosí in Mexico provide …
Le Centre antifraude du Canada produit des bulletins régulièrement pour aider les Canadiens à mieux se protéger contre la fraude. Le présent bulletin donne les grandes lignes de la fraude sans carte, qui continue de cibler des entreprises canadiennes. Il décrit aussi les diverses tendances associées à ce type de fraude ainsi que les indices …
The Canadian Anti-Fraud Centre produces regular bulletins to help Canadians to better protect themselves against fraud. This bulletin was prepared to provide awareness on Card-Not-Present (CNP) Fraud, which continues to target Canadian businesses. It depicts the trends and patterns associated to the fraud, as well as warning signs to prevent victimization. Overview CNP Fraud …
A rowhammer attack exploits a vulnerability created by the physical characteristics of modern computer memory. Dynamic Random-Access Memory (DRAM) is a high-speed memory circuit that stores information by creating an electrical charge in tiny capacitor; which is something like a battery. A charged capacitor represents a value (i.e.”1”) as opposed to an uncharged capacitor (“0”). …
People often make predictable passwords. They use common methods to create passwords such as common words, substituting characters or using patterns on the keyboard. Blase Ur from the University of Chicago and a team from Carnegie Mellon University developed and evaluated a password security meter that provides a more accurate rating of password strength and …
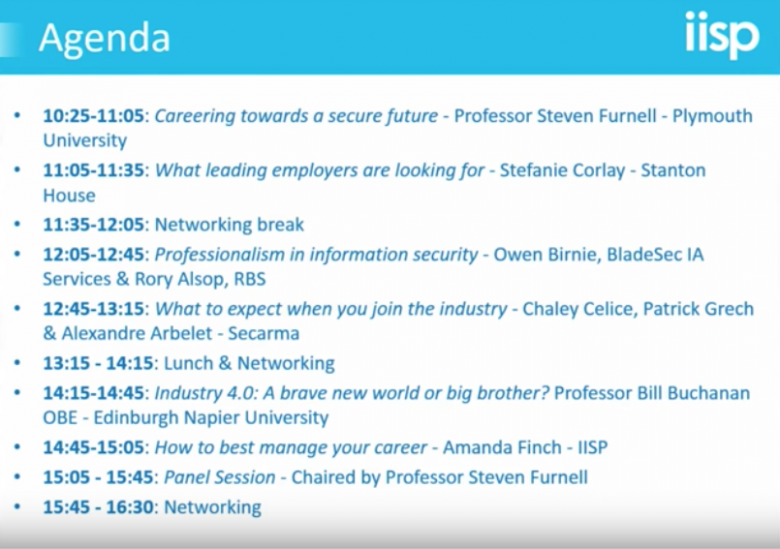
The IISP (Institute of Information Security Professionals) and our friends the Cyberacademy at Napier College, Edinburgh, Scotland recently (2017/11/23) held an event for those looking to start or continue a career in cybersecurity. The event had a number of great presenters and fortunately for us was streamed to youtube. The full video is over 5 …
Governments around the world are being increasingly trapped between progress to a digital state and the insecurity of cyberspace. Estonia has been a vanguard for development of a digital society in many ways by transitioning many services to digital technologies and also by being subject to assault by cyber weapons. Nick Robinson and Prof Keith …
Nour Dabbour from Carleton University presented a 2 minute rapid-fire of her poster at the SERENE-RISC workshop October, 2017. Rapid fire presentations are limited to 2 minutes and 1 slide. Nour was voted as the winner of the student poster presentations at this event by the SERENE-RISC membership in attendance. Do I know you? …