In the last decade, many studies have tried to understand and explain the motivations behind the commission of cybercrimes. However, to date, no study has sought to explain the effect of personality on individual differences in the very motivations for engaging in cybercrime.
For this reason, researchers Palmieri, Shortland, and McGarry (2021) decided to focus their research on the study of personalities using the reinforcement sensitivity theory (RST) from Gray (1982; 1987). This theory of motivation postulates that individuals all have different responses to their environment that arise from different sensitivities of the primary brain systems, which all respond to either rewarding or punitive stimuli (Gray, 1973). Gray’s (1973) framework involves three systems (Behavioral Activation System (BAS), Behavioral Inhibition System (BIS), Fight-or-Flight System (FFS)), which all explain the differential sensitivities influencing reward behaviours, punishment, and threat-response. Considering that this theory is being used in several criminological studies to explain offline criminal behaviour, researchers then opted for this theory to explain cybercrime behaviour as a plausible hypothesis.
A total of 577 participants completed the RST Personality Questionnaire (RST-PQ). To participate in the study, they all had to admit that they have been involved in one of the cybercriminal behaviours listed by Donner et al. (2014):
(1) post hurtful information about an individual on the Internet; (2) threaten/insult others via email or instant messaging; (3) exclude someone from the online community; (4) hack into an unauthorized area of the Internet; (5) distribute malware; (6) illegally download copyrighted files/programs; (7) illegally download copyrighted files/programs; (8) use someone’s personal information others on the Internet without their permission; (9) using the Internet to facilitate a drug transaction, and (10) posting nude photos of someone else without their permission (p. 167-168). In Table 1, it is possible to observe the percentage of the sample of participants distributed in the ten cyber acts committed in the past.
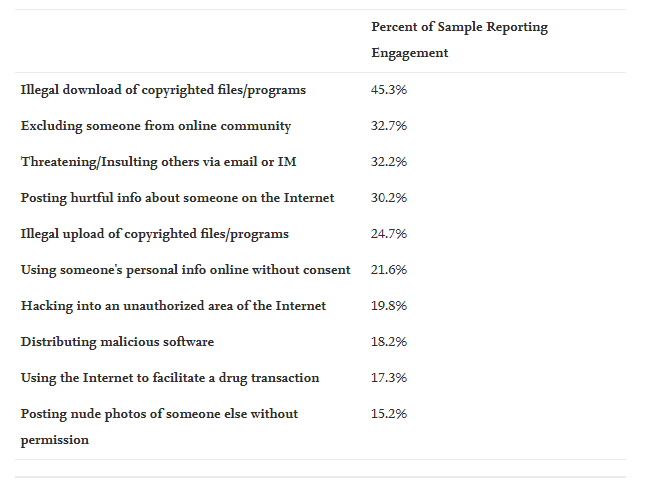
Table 1. Sample reports of engagement in specific cybercrimes
The study’s results confirmed the hypothesis that traits related to RST were associated with cybercrime. Additionally, the four BAS sub-factors (Reward Interest, Goal Persistence, Reward Responsiveness, and Impulsivity) were found to have different relationships with cybercrime. BIS traits were also positively associated with cybercrime, possibly due to greater online anonymity on BIS’s role as a conflict mediator. In short, this article provides a better understanding of the contribution of personality to the motivations of criminals engaging in activities related to cybercrime.
This study supports the application of RST to the study of cybercrime. However, the researchers mentioned the need and relevance of focusing future research on (1) disaggregating the varying effects of BAS activation on engagement in specific types of cybercriminal behaviour and (2) further exploring the unique effect of online anonymity on RST processes that motivate deviant behaviour online.
To cite: Palmieri, M., Shortland, N., McGarry, P. (2021). Personality and online deviance: The role of reinforcement sensitivity theory in cybercrime. Computers in Human Behavior, 120. https://doi.org/10.1016/j.chb.2021.106745




