The Internet of Things (IoT), cloud computing technology, and health technologies are essential tools in 2021 to ensure the well-being and running of individuals and organizations’ activities in our society. However, considering the importance of connected objects and the irreplaceable place they occupy, it is vital to ensure that they are well protected against malware threats. As seen in the past, malicious individuals can hack connected objects, such as a pacemaker (Schaer, 2018). This act can inevitably lead to the death of a human.
Researchers Podder et al. (2020) focused their research objectives on security threats on connected objects considering these considerable stakes. The figure below visualizes and summarizes everything that the IoT, including cloud technology, implies.
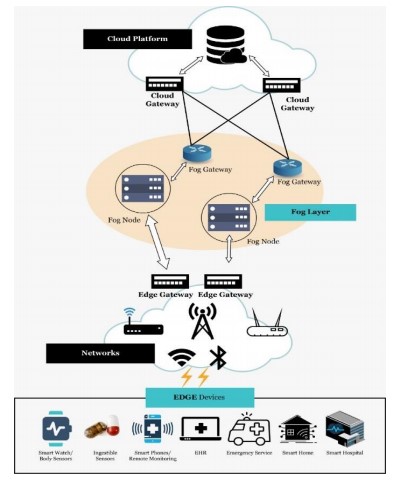
Here are the main contributions of this article:
1) The authors describe IoT application in industrial and medical service scenarios, such as emergency services and technologies enabling human functioning (example: a pacemaker).
2) Security threats are discussed for the different layers of the IoT health architecture (see figure 2).
3) They discuss the different types of malware (see figure 3) like spyware, viruses, worms, keyloggers, trojan horses, and more.
4) They give concrete examples of past events where malware has disrupted activities in the healthcare system or other essential business areas, for instance, Mirai, Echobot, and Reaper.
5) Researchers are discussing ways to protect against malware, such as the use of K-plus and kNN machine learning algorithms. 6) The various tools for detecting, classifying, and analyzing ransomware are also examined.
Notably, this scientific article has a considerable contribution for researchers and practitioners in the health sector who wish to learn more about the risks and means of protection in the face of security threats on connected objects that are part of the IoT. Furthermore, according to these IoT security researchers, the future scopes are set in terms of conclusion and open the discussion on interesting solutions.
To cite: Podder, P.P, Mondal, R.H., Bharati, S., Paul, P.K. (2020). Review on the Security Threats of Internet of Things, International Journal of Computer Applications, 176, 41. DOI: 10.5120/ijca2020920548
Schaer, K. (2018, 13 août). Des hackers démontrent qu’un pacemaker peut être aisément piraté. Médecine, ma RTS. https://www.rts.ch/info/sciences-tech/medecine/9772308-des-hackers-demontrent-qu-un-pacemaker-peut-etre-aisement-pirate.html