Digital Forensics is a challenging field due to the mixture of computer science and law knowledge required. Combining these in a teachable format is challenging. The use of a traditional lectures for the conceptual preparation required for for hands-on digital forensics labs and exercises can be less than desired. William Johnson, Irfan Ahmed, Vassil Roussev …
The utopian vision of cyberspace saw us move beyond all the limitations of the physical. Transcendent beings of light we would leave behind greed, hate and discrimination. Is this fictional future possible, or are we destined to bring our faults with us into cyberspace? Are our online services countering or contributing to discrimination online. Karent …
Apple Pay was launched more than 3 years ago to provide a “fast and secure” method of payment and quickly became very popular in the US. It was shortly followed by Android Pay which is also becoming popular. However, not everyone uses these systems despite their claimed security, convenience and speed. Jun Ho Huh, Saurabh …
The sharing of intimate images by digital means is something that has created new issues for Canadians. This is reflected in the creation of laws for non-consensual intimate image sharing or ‘revenge porn’ laws. The issues get murkier when it comes to intimate images and youth as child pornography laws often also apply to the …
Never mind sophisticated and persistent threats, what about simple and opportunistic ones? Have we closed the door on attacks that require little investment on the part of attackers? In particular, are we still shipping software without the most basic of security policies ? B. Knieriem, X. Zhang, P. Levine, F. Breitinger & I. Baggili surveyed …
There is a considerable amount of evidence on the control and censorship of social media in China. On top of this there has long been suspected that there is a system of astroturfing, or the posting of large numbers of comments from fake accounts to direct online conversation. In China people hired to make these …
Jonathon Lusthaus and Federico Varese provide more insight into the phenomena of online crime groups. To provide more of an understanding of the offline nature of online groups they took two field trips to Romania to investigate the region around Râmnicu Vâlcea, a local known for cybercrime. The Region of Ca Piteşti, which contains this …
A group from Northwest University, China, and the University of Bath and Lancaster University in the UK have come up with a method for determining android unlock patterns. The method uses video footage captured by a smartphone and an algorithm that can determine likely codes that match the movement of the finger or hand across …
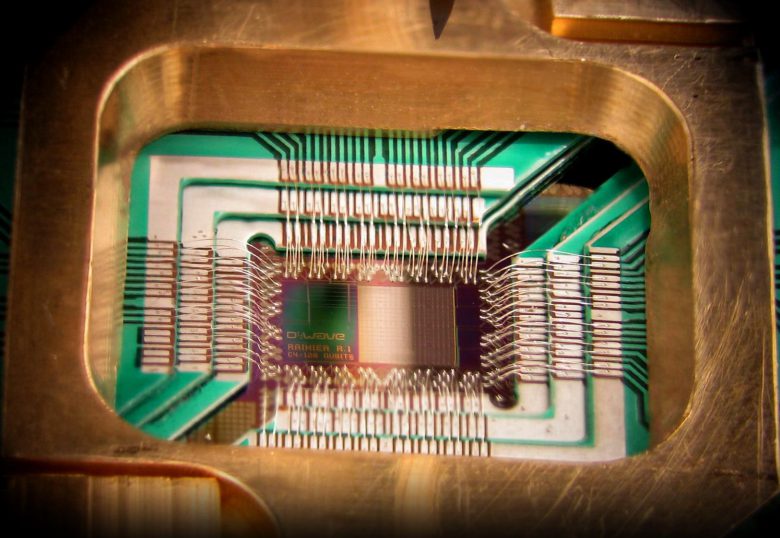
Dr. Michele Mosca reminds us an unfortunate truth as laid bare by Max Planck “A new scientific truth does not triumph by convincing its opponents and making them see the light, but rather because its opponents eventually die, and a new generation grows up that is familiar with it.” Quantum Computing is an area …
Highly secure systems are often ‘Air Gapped’, or removed from any internet connected network to make it more difficult to illegally or maliciously access them. Attacks in recent years have shown that it is possible and perhaps not even particularly complex to have users load malicious software onto an air gapped computer (e.g. with a …