Political parties are an essential part of electoral democracy. They have also been identified by the intelligence community and academic researchers as a weak point in the cybersecurity of many democracies. The hacking of the Democratic National Committee’s emails is one prominent example of how ineffective cybersecurity by a political party can have far-reaching implications. …
(English version will follow) PROFIL DE COMMUNAUTÉ Le réseau SERENE-RISC désire partager avec ses membres des profils de personnes oeuvrant dans le domaine de la cybersécurité. Le Réseau se veut être un lieu d’échange d’information sur la cybersécurité à la fois ouvert, impartial et inclusif. À travers ces profils, SERENE-RISC offre cette opportunité d’échange afin …
(French below) Every year more and more people are doing their Christmas shopping online. Online Christmas shopping can come as blessing, as you can beat the queues in stores and get it all delivered to your door without leaving your house. However there are risks associated with online shopping. Cybersecurity challenges are continually evolving and …
In Canada, there are both legislative gaps and ambiguity around the privacy obligations of political parties with respect to voter data. Despite the highly sensitive nature of political preferences, political parties have been largely exempt from formal obligations to protect personal information. Privacy legislation requires that entities adhere to fair information principles, which require notice …
The workplace is a radically different environment since Information Systems (IS) became one of the strongest enablers for its processes. But IS can be misused. Security issues in IS are becoming more prevalent than ever before. In addition to the significant damage of these acts, the stakeholders deemed accountable for these events have faced severe …
Accounts of social network users can be compromised in a number of ways. When malware infects a user account, that account can be used to spread spam and malware as well as to gather personal information. Current online systems employ authentication mechanism to verify user’s identities and determine their corresponding authorities. Once authenticated, users are …
Les enfants utilisent de plus en plus d’appareils portables pour aller en ligne. Il est donc important de les éduquer sur les manières de se protéger. Ces appareils ainsi que les applications qui y sont installés disposent parfois de GPS et autres outils de géolocalisations pouvant mettre les enfants à risque d’être victimes de vol …
A Privacy Enhanced Facial Recognition Access Control System Using Biometric Encryption Biometric authentication is seen as a mixed offering, the ease and comfort of a system that knows who you are without you having to work to prove it (as with a password) is balanced against the need to store personal information and the potential …
Information Security Policy Compliance: An Empirical Study of Rationality-Based Beliefs and Information Security Awareness Burcu Bulgurcu and researchers from the Saunders School of Business at the University of British Colombia looked into the problem of employees not complying with security policy. Security policy is (generally) put in place to protect the company from attacks directed …
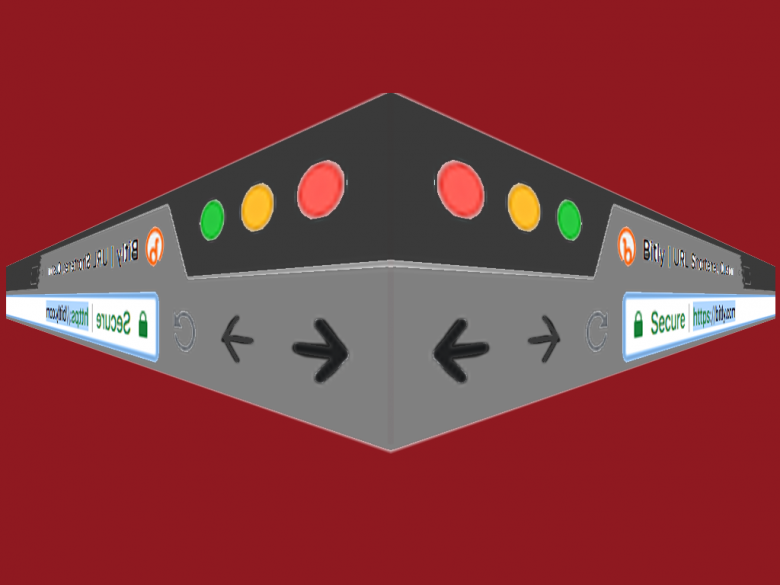
URL shortening services provide a short link in place of a long URL. Attackers sometimes use these services to mask the URL of a malicious destination, making it harder for a person to detect a link that they shouldn’t click on. A group from the university of Ottawa and IBM collected 300 thousand malicious …