The number of phishing attacks continues to increase. Although citizens are more and more aware of it, this type of scam is still very profitable for criminals. A phishing-type attack aims to trick victims into clicking on a link leading them to a malicious website or one imitating a legitimate one. Once on this cloned site, victims have to fill in their information, like their username, password, and sometimes their date of birth and valuable information such as their credit card number, or worse yet, their social assurance number. The cloned pages can be very realistic, resembling popular pages like Facebook, Instagram, Twitter, Yahoo, Gmail, and more. The malicious link can be sent to thousands of victims either by email or text message. For example, in the context of COVID-19, cybercriminals used the situation to reach even more victims by text message alarming them that the government needed their information or wanted to send them money and that to do so, they had to log in via a fake government page.
Also, criminals do not just prey on the general population; company CEOs have been trapped, as have IT staff on the cybersecurity team. Although companies predominantly provide cybersecurity awareness training, hackers are too often successful in overriding human defences in multiple ways. This phenomenon’s leading cause would be the overload of employees’ tasks and expectations, which are only becoming more complex and demanding. Simultaneously, emails are becoming more realistic, and so are the login details on fraudulent pages, making it even more difficult for victims to differentiate real ads from fake ones. For example, the following image is a screenshot of a fake Instagram page, used to trick users. Once the victims identify themselves on this page, the perpetrators have access to their information.

The authors of this scientific article focused on the reasons that influence phishing attacks’ success and, more importantly, how to prevent them.
They examined more than 300 phishing emails received by Gmail or Yahoo to identify the fifteen most common tactics (Table 1). They reviewed best cybersecurity practices, especially the best advice to provide to company employees to identify scams by email or text message.
Table 1: Features for phishing detection
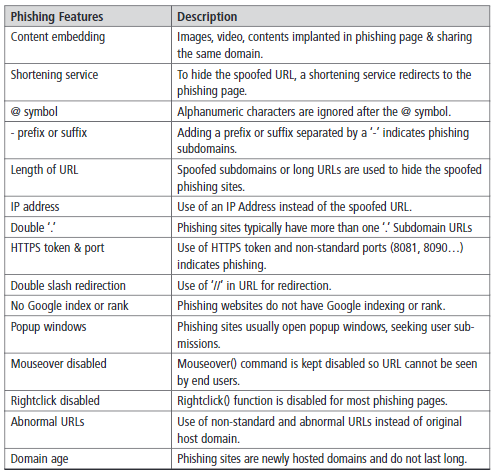
According to the authors, employers must make sure their employees receive this information to detect phishing attacks in the workplace and for their well-being.
In summary, the authors state that one of the main reasons for phishing attacks being successful is the lack of individuals’ training to deal with the problem. As mentioned earlier, it is too often due to a human flaw that cyber-attacks are successful. Employees need to have practical resources so that they can identify attacks on the spot. This study highlights the importance companies must place on training and educating their employees about its attacks. It is undeniable that phishing attacks are very profitable for criminals as it still is today. Therefore, companies must be resilient and adequately train their employees.



