Canadian businesses continue to embrace digital technologies rapidly, exposing them to a greater range of cybersecurity risks and threats. The 2017 Canadian Survey of Cyber Security and Cybercrime (CSoCC) was designed to provide a portrait of the current threat environment by providing new and up-to-date information Canadian businesses’ responses to cybersecurity challenges.
Canadian businesses and their cybersecurity measures
The Survey examined eleven types of cybersecurity measures in place by industry and enterprise size [1]:
- Mobile security (management of personally-owned devices, secure remote access, virtual private network (VPN))
- Anti-malware software to protect against viruses, spyware, ransomware, et cetera (Microsoft Security Essentials, Malwarebytes, Symantec Endpoint Protection)
- Web security (digital certificates, website restrictions)
- Email security (spam filters, email scans)
- Network security (firewalls, proxy servers, honeypot systems)
- Data protection and control (encryption, rights management)
- Point-Of-Sale (POS) security (encryption of cardholder data)
- Software and application security (application whitelisting, scheduled patching)
- Hardware and asset management (inventory of information technology (IT) equipment, encrypted universal serial bus (USB) storage devices)
- Identity and access management (password complexity rules, restrictions based on user accounts)
- Physical access controls (keypad access control systems, identity badges)
According to the Survey, 20.8% of Canadian businesses were impacted by a cybersecurity incident, which affected their operations[2]. These numbers are probably underestimated, as many companies might not have the technical capacity to detect the most sophisticated and persistent attacks, that can unfold over many months. Indeed, few companies are able to protect effectively their assets, often due to budget constraints, lack of knowledge of the available tools, lack of professional expertise, and unclear management directions. Technological changes such as cloud computing, e-commerce, working from home and “Bring your own device” policies, further increase the potential for attacks.
The issue
As explained here, the Survey is an important tool for building a more resilient Canadian ecosystem and market. For this reason, SERENE-RISC explores the many uses that can be made of the survey data. This week, we examine the (un)popular cybersecurity measures implemented by Canadian companies.
The aggregate results of the CSoCC for cybersecurity measures
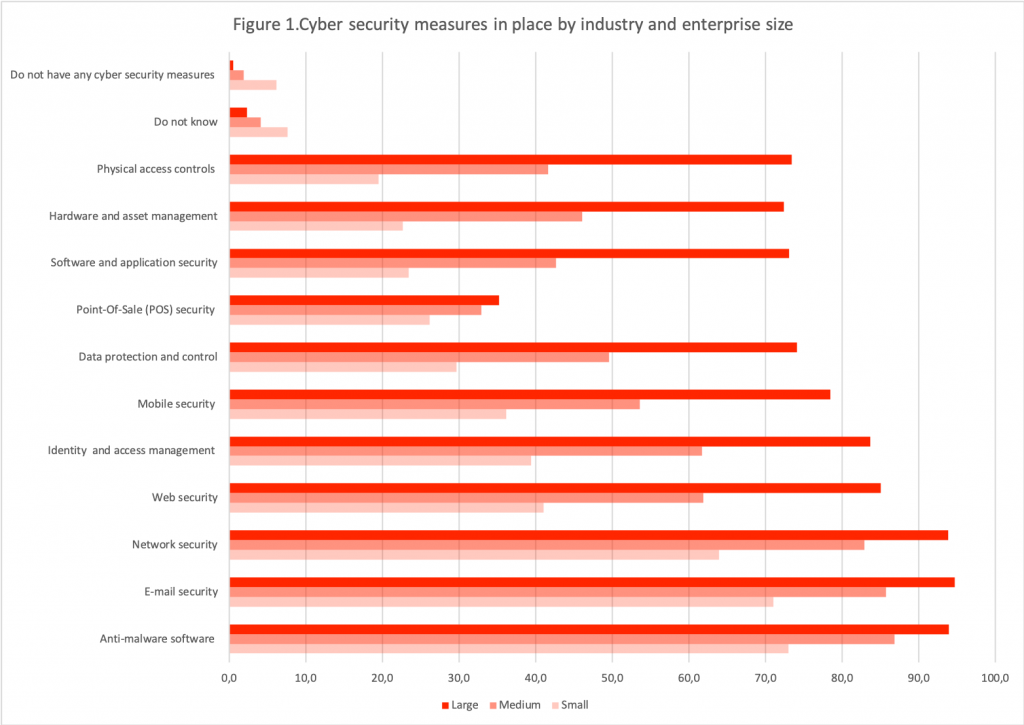
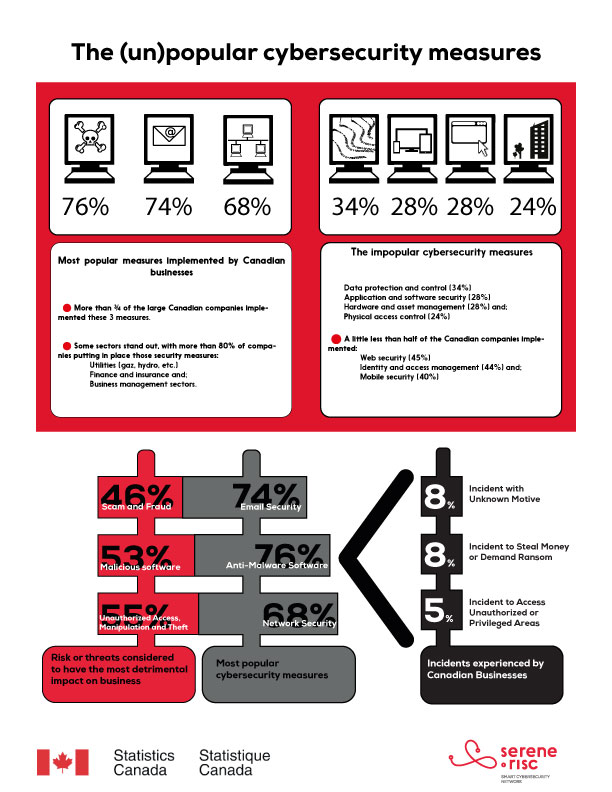
The aggregate results of the Survey showed that anti-malware software (75.8%), e-mail security such as spam filter (73.9%) and network security such as firewall and honeypot systems (67.7%) are the most popular measures implemented by Canadian companies of all sizes and sectors. Indeed, more than ¾ of the large Canadian companies implement these measures. Some sectors stand out, such as the utilities (electric power generation, natural gas distribution, etc.) , the finance and insurance and the business management sectors, with more than 80% of companies put in place the security measures. It is worth pointing out that for measures such as web security (45.4%), identity and access management (44.1%) and mobile security (40%), a little less than half of the Canadian companies implement these measures (see fig. 1). The results regarding the mobile security is noteworthy particularly because 66% of Canadian companies allow their employees to bring their own devices to work.
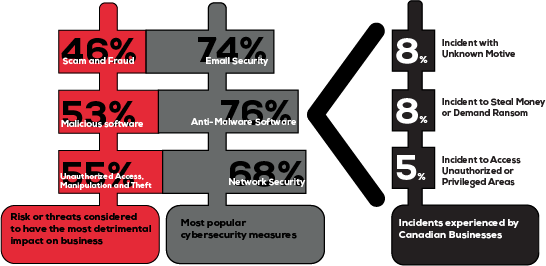
Yet, the highest percentage of incidents is for unknown incidents (8.1%), theft of money or ransom (8.0%) and unauthorized access (5.3%)[3]. Furthermore, the risks or threats considered to have a negative impact[4] are related to the measures put into place (unauthorized access, malware software, and scams and frauds), not to the reported incidents types (see fig. 2). In sum, it seems that the measures put in place by Canadian businesses depend more on what is being feared (perceived risks) rather than what is actually happening.
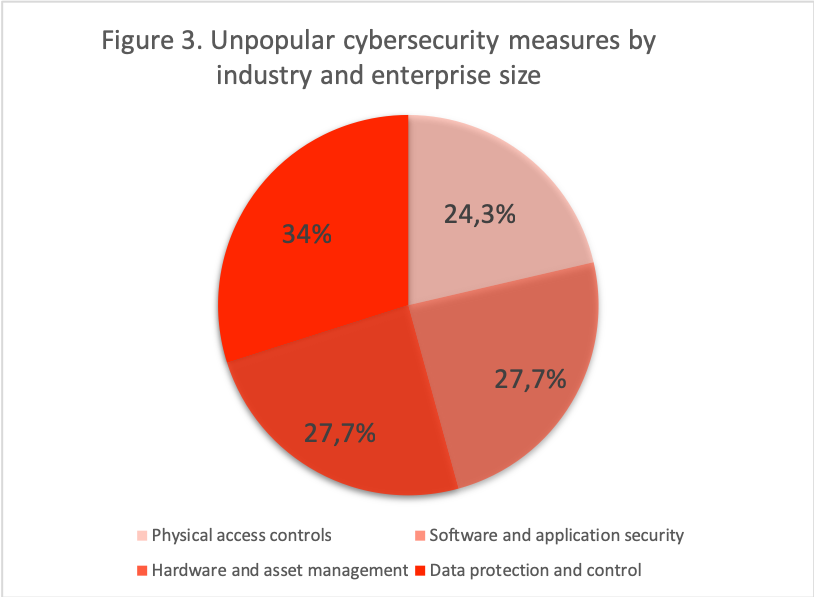
The CSoCC also shows that Canadian companies invested less in data protection and control (34%), application and software security (27.7%), hardware and asset management (27.7%) and physical access control (24.3%) (see fig. 3). Some companies in the utilities, finance, insurance and corporate management sectors stand out, but again, the adoption of these measures remains weak: just over half of these companies are adopting the measures.
What research says about the most (un)popular measures?
Malware is a common source of attacks which spreads easily and quickly, especially through the email. Anti-malware software is thus an effective tool for detecting and deterring malware attacks.[5] Not surprisingly, anti-malware software is among the most popular measure implemented by Canadian businesses, particularly when we keep in mind that incidents related to security breaches create fear and strengthen the willingness for better protection. The more individuals perceive a response as effective, the more likely they are to put that response in place[6].
Regarding the less popular measures, several studies show that for organizations, updating software and installing patches necessary for software security and application is not a priority since the threats posed appear less visible[7]. Also, the importance and recurrence of data theft and their related impact on reputation and customer confidence, shows the need for companies to better protect their data. In addition, devices management might be necessary, since it is difficult to implement good measures with no clear understanding of what should be secured[8].
Finally, employees increasingly use their own devices, which can compromise the corporate network when reconnected to the system. Given that companies invest less in measures to protect mobile security they might think about building a more holistic approach.
Concluding remarks
It appears that the measures implemented by Canadian businesses are not always in tune with the actual incidents experienced. Perhaps those measures are fulfilling their role in ensuring that the incidents they are supposed to prevent become a marginal risk.
The Survey suggested that Canadian businesses would benefit from a more holistic approach to cybersecurity when it comes to cybersecurity measures. In this regard, cybersecurity risks assessments processes are important steps before engaging in cybersecurity measures.
Download the infographic of the article in a PDF file