Political parties are an essential part of electoral democracy. They have also been identified by the intelligence community and academic researchers as a weak point in the cybersecurity of many democracies. The hacking of the Democratic National Committee’s emails is one prominent example of how ineffective cybersecurity by a political party can have far-reaching implications. …
(English version below) Pour Noël, vous avez certainement planifié de vous acheter ou d’offrir un des nombreux assistants vocaux disponibles sur le marché. De plus en plus de gens achètent ce type d’appareil ainsi que des appareils intelligents pour des raisons de commodité et de sécurité. Les interactions informatiques activées par la voix sont intégrées …
The National Cybercrime Coordination Unit (NC3) Unit was funded in Budget 2018 as part of Canada’s Cyber Security Strategy. Assistant Commissioner Adam will cover the formulation of the impetus behind the creation of this unit, and its mandate and concept of operations. About the speaker Jeff Adam completed 14 years of operational policing in New …
The security of elections is a key issue for the defence communities around the globe. Recent examples make the urgency of this issue clear: the 2017 Presidential elections in Kenya were declared invalid amidst allegations of problems with the electoral commission’s databases and computers; Estonia’s widely respected identity card system, which is used for i-voting …
(English version will follow) PROFIL DE COMMUNAUTÉ Le réseau SERENE-RISC désire partager avec ses membres des profils de personnes oeuvrant dans le domaine de la cybersécurité. Le Réseau se veut être un lieu d’échange d’information sur la cybersécurité à la fois ouvert, impartial et inclusif. À travers ces profils, SERENE-RISC offre cette opportunité d’échange afin …
(French below) Every year more and more people are doing their Christmas shopping online. Online Christmas shopping can come as blessing, as you can beat the queues in stores and get it all delivered to your door without leaving your house. However there are risks associated with online shopping. Cybersecurity challenges are continually evolving and …
In Canada, there are both legislative gaps and ambiguity around the privacy obligations of political parties with respect to voter data. Despite the highly sensitive nature of political preferences, political parties have been largely exempt from formal obligations to protect personal information. Privacy legislation requires that entities adhere to fair information principles, which require notice …
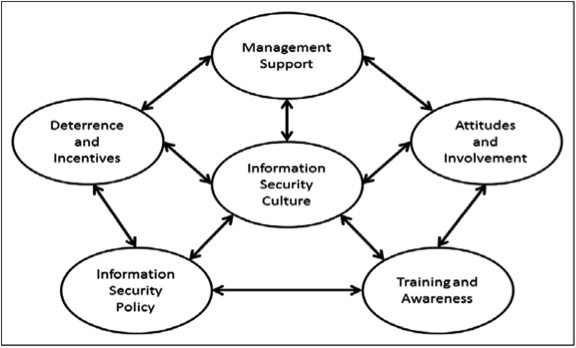
Nowadays, organizations collect, transmit, and use data to perform a variety of business-related functions. The proliferation of data makes organizations targets for cyber criminals. This threat has resulted in large investments in secure data storage, networks, and cyber-defense systems. In spite of these investments, cybercrime is still very prevalent with massive breaches being reported almost …
The workplace is a radically different environment since Information Systems (IS) became one of the strongest enablers for its processes. But IS can be misused. Security issues in IS are becoming more prevalent than ever before. In addition to the significant damage of these acts, the stakeholders deemed accountable for these events have faced severe …
Les menaces liées au cybercrime ont créés une augmentation importante de dépenses en surveillance et logiciels de la part des compagnies et gouvernements pour se protéger contre toutes ces menaces. Cependant, ils occultent souvent un des risques premiers à la cybersécurité : les utilisateurs. Les utilisateurs ordinaires, et non les technologies, sont souvent décrits comme la …